ITTIA SDL Is Conformant to the Principles of IEC/ISO 62443
ITTIA DB security shields edge devices; manufacturers thrive under certainty
ITTIA security practices and features assist manufacturers of IoT edge devices with advanced and integrated software development methods, infused by a secure development life cycle based on zero trust principles, enabling makers of IoT edge devices to mitigate unpredictability. From product conception to end-of-life, ITTIA adheres to a secure-by-design development methodology, and ITTIA DB offers a complete solution to secure data on IoT devices.
ITTIA’s Solution for Data Management Threats
In general, devices must be open to data collecting and sharing, and this is where the danger lies. Because embedded system security mandates the protection of sensitive data throughout the device's life cycle, secure storage and transmission become vital. As a result, a multi-dimensional security technique is required for device internal data management, data protection risks, attack taxonomy, and system vulnerabilities.
Data encryption, authentication, ITTIA DB Security Expert Agent Library (DB-SEAL), and consulting to support hardware security modules are among the security features offered by ITTIA. From a business standpoint, ITTIA is open to communicate its confidential data security policies and practices with customers.
SQL injections are one of the most prevalent database attacks. The injection of malicious code into the device and the execution of malicious queries are two examples. SQL control hijacking is a form of attack that diverts the normal control flow of the programs running on the device, usually resulting in the hacker injecting SQL code.

SQL code execution is a method by which attackers feed code to an embedded device, such as web scripts and SQL injections, that is not native to the device's application. These attacks result in a variety of issues, including integrity violations, which are a regular side effect of new codes on a device's database. This assault could result in changes to configuration settings, data, or even firmware updates that aren't legal. In extreme situations, the effect may even result in the disclosure of sensitive information.
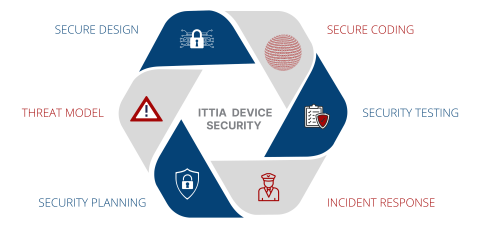
ITTIA Secure Development Lifecycle Overview
In the embedded world, it is vital that organizations can deploy their solutions knowing that the technology they rely on is developed with security at the forefront. To help ensure this level of confidence, ITTIA has embedded security awareness and practices throughout product development. This is achieved through the ITTIA Secure Development Lifecycle (ITTIA SDL.)
- Security Planning – Security planning and training
- Threat Model – Identify and prioritize product security risks
- Secure Design – Security considerations are built in by design
- Secure Coding – Static analysis and coding standards
- Security Testing – Vulnerability and penetration testing
- Incident Response – Vulnerability handling and communication
Security Planning
The planning phase is critical to gain an overview of security needs for products, development environment, and personnel. Security planning encompasses developer training on best practices for secure design and coding. It also includes defining overall product security requirements spanning across features, validation, and tools. Clear roles are established, ensuring separation between security development vs. validation activities. Lastly, part of the planning is to validate system and development infrastructure meets stringent security requirements.
Threat Model
Security threat modeling allows us to identify potential security risks and gives us a better understanding of the product’s attack surface and threat boundaries. The threat model evolves as capabilities are added, modified, or removed in product releases.
Our developers leverage the use of threat modeling tools to generate information around security risks. This information allows us to create and implement strategies to address these risks and reduce the product attack surface. It also serves as the reference to continuously adapt the security testing aspects of the product.
Secure Design
Product security is enhanced significantly when security considerations are reviewed and identified in the earliest phase of feature development. All new product requirements include a review of security impacts and best practices.
It is critical to protect sensitive data in a data management system from unintended disclosure and alteration. We use and provide a variety of encryption standards to protect against unauthorized access and modification of the data. Our proprietary security expert agent can also be used to train the system on normal device data management behavior before deployment. The system is then able to react and stop any unfamiliar attempt in accessing the data.
We enforce stringent criteria when considering the use of any third-party software in our products. Any proposed third-party software usage is reviewed before selection to ensure they meet the security requirements of the system. Third-party software is also covered by our security incident response policy.
Secure Coding
We use static analysis tools during development to analyze weaknesses in the code that might lead to vulnerabilities. Examples include dangerous inputs and buffer overflows, among others. Our product APIs are designed to enforce safe practices in application code that uses our software libraries. The APIs check that the application binds the right size buffers for each database type. We follow updated coding standards for the programming languages used in the product. These standards are checked through code analysis tools. All development is performed and stored in secured source control repositories. This also allows our software developers to perform peer reviews that help strengthen the quality and security of the code.
Security Testing
Our security vulnerability testing enhances the resiliency of our products against potential attacks. We combine feature robustness testing with the use of tools that test for common attacks and scans. Our security penetration testing team performs various scenarios, leveraging various tools, to simulate the actions of potential attackers. The objective is to uncover coding and operational weaknesses in the products. Fuzz testing is used to ensure our capabilities and interfaces are resilient when injected with invalid, malformed, or unpredictable inputs and stress.
Incident Response
A critical component to any secure development lifecycle is having a well-documented security incident response policy that is followed. Our security incident response policy ensures customers and organizations can report potential vulnerabilities to us. We also actively monitor and assess well-known vulnerabilities that are publicly reported. In the case our products are confirmed to be vulnerable to a security incident, our security response team will strive to provide corrective action as quickly as possible. The team will also ensure effective communication of incident status and remediation through all appropriate channels.
Reporting a Security Vulnerability
In the event where a security vulnerability is found in any of our products, we ask that you report to us as soon as possible. ITTIA has established an email address that should be used to report vulnerabilities. Please send a full description of the vulnerability, instructions to reproduce, and product information to security [at] ittia.com (security[at]ittia[dot]com). Please include all relevant details as far as software and hardware configuration.
Getting Started
During the software development process, ITTIA DB professionals help customers identify and prioritize the required edge device data security relevant to individual applications, as well as offer training on ITTIA DB security features and security practices.